Removing Backdoor-Based Watermarks in Neural Networks with Limited Data
Xuankai Liu,
Fengting Li,
Bihan Wen,
Qi Li
Auto-TLDR; WILD: A backdoor-based watermark removal framework using limited data
Similar papers
Delving in the Loss Landscape to Embed Robust Watermarks into Neural Networks
Enzo Tartaglione, Marco Grangetto, Davide Cavagnino, Marco Botta

Auto-TLDR; Watermark Aware Training of Neural Networks
Abstract Slides Poster Similar
Beyond Cross-Entropy: Learning Highly Separable Feature Distributions for Robust and Accurate Classification
Arslan Ali, Andrea Migliorati, Tiziano Bianchi, Enrico Magli

Auto-TLDR; Gaussian class-conditional simplex loss for adversarial robust multiclass classifiers
Abstract Slides Poster Similar
Adaptive Noise Injection for Training Stochastic Student Networks from Deterministic Teachers
Yi Xiang Marcus Tan, Yuval Elovici, Alexander Binder

Auto-TLDR; Adaptive Stochastic Networks for Adversarial Attacks
Attack Agnostic Adversarial Defense via Visual Imperceptible Bound
Saheb Chhabra, Akshay Agarwal, Richa Singh, Mayank Vatsa

Auto-TLDR; Robust Adversarial Defense with Visual Imperceptible Bound
Abstract Slides Poster Similar
Verifying the Causes of Adversarial Examples
Honglin Li, Yifei Fan, Frieder Ganz, Tony Yezzi, Payam Barnaghi

Auto-TLDR; Exploring the Causes of Adversarial Examples in Neural Networks
Abstract Slides Poster Similar
P-DIFF: Learning Classifier with Noisy Labels Based on Probability Difference Distributions
Wei Hu, Qihao Zhao, Yangyu Huang, Fan Zhang

Auto-TLDR; P-DIFF: A Simple and Effective Training Paradigm for Deep Neural Network Classifier with Noisy Labels
Abstract Slides Poster Similar
A Delayed Elastic-Net Approach for Performing Adversarial Attacks
Brais Cancela, Veronica Bolon-Canedo, Amparo Alonso-Betanzos

Auto-TLDR; Robustness of ImageNet Pretrained Models against Adversarial Attacks
Abstract Slides Poster Similar
Large-Scale Historical Watermark Recognition: Dataset and a New Consistency-Based Approach
Xi Shen, Ilaria Pastrolin, Oumayma Bounou, Spyros Gidaris, Marc Smith, Olivier Poncet, Mathieu Aubry

Auto-TLDR; Historical Watermark Recognition with Fine-Grained Cross-Domain One-Shot Instance Recognition
Abstract Slides Poster Similar
Meta Soft Label Generation for Noisy Labels
Auto-TLDR; MSLG: Meta-Learning for Noisy Label Generation
Abstract Slides Poster Similar
Neuron-Based Network Pruning Based on Majority Voting
Ali Alqahtani, Xianghua Xie, Ehab Essa, Mark W. Jones
Auto-TLDR; Large-Scale Neural Network Pruning using Majority Voting
Abstract Slides Poster Similar
Local Clustering with Mean Teacher for Semi-Supervised Learning
Zexi Chen, Benjamin Dutton, Bharathkumar Ramachandra, Tianfu Wu, Ranga Raju Vatsavai

Auto-TLDR; Local Clustering for Semi-supervised Learning
Generative Latent Implicit Conditional Optimization When Learning from Small Sample
Auto-TLDR; GLICO: Generative Latent Implicit Conditional Optimization for Small Sample Learning
Abstract Slides Poster Similar
Variational Inference with Latent Space Quantization for Adversarial Resilience
Vinay Kyatham, Deepak Mishra, Prathosh A.P.

Auto-TLDR; A Generalized Defense Mechanism for Adversarial Attacks on Data Manifolds
Abstract Slides Poster Similar
How Does DCNN Make Decisions?
Yi Lin, Namin Wang, Xiaoqing Ma, Ziwei Li, Gang Bai

Auto-TLDR; Exploring Deep Convolutional Neural Network's Decision-Making Interpretability
Abstract Slides Poster Similar
Optimal Transport As a Defense against Adversarial Attacks
Quentin Bouniot, Romaric Audigier, Angélique Loesch

Auto-TLDR; Sinkhorn Adversarial Training with Optimal Transport Theory
Abstract Slides Poster Similar
Defense Mechanism against Adversarial Attacks Using Density-Based Representation of Images
Yen-Ting Huang, Wen-Hung Liao, Chen-Wei Huang
Auto-TLDR; Adversarial Attacks Reduction Using Input Recharacterization
Abstract Slides Poster Similar
F-Mixup: Attack CNNs from Fourier Perspective
Xiu-Chuan Li, Xu-Yao Zhang, Fei Yin, Cheng-Lin Liu

Auto-TLDR; F-Mixup: A novel black-box attack in frequency domain for deep neural networks
Abstract Slides Poster Similar
MINT: Deep Network Compression Via Mutual Information-Based Neuron Trimming
Madan Ravi Ganesh, Jason Corso, Salimeh Yasaei Sekeh
Auto-TLDR; Mutual Information-based Neuron Trimming for Deep Compression via Pruning
Abstract Slides Poster Similar
Overcoming Noisy and Irrelevant Data in Federated Learning
Tiffany Tuor, Shiqiang Wang, Bong Jun Ko, Changchang Liu, Kin K Leung

Auto-TLDR; Distributedly Selecting Relevant Data for Federated Learning
Abstract Slides Poster Similar
Accuracy-Perturbation Curves for Evaluation of Adversarial Attack and Defence Methods
Auto-TLDR; Accuracy-perturbation Curve for Robustness Evaluation of Adversarial Examples
Abstract Slides Poster Similar
Iterative Label Improvement: Robust Training by Confidence Based Filtering and Dataset Partitioning
Christian Haase-Schütz, Rainer Stal, Heinz Hertlein, Bernhard Sick

Auto-TLDR; Meta Training and Labelling for Unlabelled Data
Abstract Slides Poster Similar
Variational Deep Embedding Clustering by Augmented Mutual Information Maximization
Qiang Ji, Yanfeng Sun, Yongli Hu, Baocai Yin

Auto-TLDR; Clustering by Augmented Mutual Information maximization for Deep Embedding
Abstract Slides Poster Similar
Learning with Multiplicative Perturbations

Auto-TLDR; XAT and xVAT: A Multiplicative Adversarial Training Algorithm for Robust DNN Training
Abstract Slides Poster Similar
Generalization Comparison of Deep Neural Networks Via Output Sensitivity
Mahsa Forouzesh, Farnood Salehi, Patrick Thiran
Auto-TLDR; Generalization of Deep Neural Networks using Sensitivity
HFP: Hardware-Aware Filter Pruning for Deep Convolutional Neural Networks Acceleration
Fang Yu, Chuanqi Han, Pengcheng Wang, Ruoran Huang, Xi Huang, Li Cui

Auto-TLDR; Hardware-Aware Filter Pruning for Convolutional Neural Networks
Abstract Slides Poster Similar
Probability Guided Maxout
Claudio Ferrari, Stefano Berretti, Alberto Del Bimbo

Auto-TLDR; Probability Guided Maxout for CNN Training
Abstract Slides Poster Similar
Rethinking Experience Replay: A Bag of Tricks for Continual Learning
Pietro Buzzega, Matteo Boschini, Angelo Porrello, Simone Calderara

Auto-TLDR; Experience Replay for Continual Learning: A Practical Approach
Abstract Slides Poster Similar
MaxDropout: Deep Neural Network Regularization Based on Maximum Output Values
Claudio Filipi Gonçalves Santos, Danilo Colombo, Mateus Roder, Joao Paulo Papa

Auto-TLDR; MaxDropout: A Regularizer for Deep Neural Networks
Abstract Slides Poster Similar
Constrained Spectral Clustering Network with Self-Training
Xinyue Liu, Shichong Yang, Linlin Zong

Auto-TLDR; Constrained Spectral Clustering Network: A Constrained Deep spectral clustering network
Abstract Slides Poster Similar
Exploiting Non-Linear Redundancy for Neural Model Compression
Muhammad Ahmed Shah, Raphael Olivier, Bhiksha Raj
Auto-TLDR; Compressing Deep Neural Networks with Linear Dependency
Abstract Slides Poster Similar
Task-based Focal Loss for Adversarially Robust Meta-Learning
Yufan Hou, Lixin Zou, Weidong Liu

Auto-TLDR; Task-based Adversarial Focal Loss for Few-shot Meta-Learner
Abstract Slides Poster Similar
Adversarially Training for Audio Classifiers
Raymel Alfonso Sallo, Mohammad Esmaeilpour, Patrick Cardinal
Auto-TLDR; Adversarially Training for Robust Neural Networks against Adversarial Attacks
Abstract Slides Poster Similar
Towards Robust Learning with Different Label Noise Distributions
Diego Ortego, Eric Arazo, Paul Albert, Noel E O'Connor, Kevin Mcguinness

Auto-TLDR; Distribution Robust Pseudo-Labeling with Semi-supervised Learning
On the Information of Feature Maps and Pruning of Deep Neural Networks
Mohammadreza Soltani, Suya Wu, Jie Ding, Robert Ravier, Vahid Tarokh
Auto-TLDR; Compressing Deep Neural Models Using Mutual Information
Abstract Slides Poster Similar
On-Manifold Adversarial Data Augmentation Improves Uncertainty Calibration
Kanil Patel, William Beluch, Dan Zhang, Michael Pfeiffer, Bin Yang

Auto-TLDR; On-Manifold Adversarial Data Augmentation for Uncertainty Estimation
Knowledge Distillation Beyond Model Compression
Fahad Sarfraz, Elahe Arani, Bahram Zonooz
Auto-TLDR; Knowledge Distillation from Teacher to Student
Abstract Slides Poster Similar
Face Anti-Spoofing Using Spatial Pyramid Pooling
Lei Shi, Zhuo Zhou, Zhenhua Guo

Auto-TLDR; Spatial Pyramid Pooling for Face Anti-Spoofing
Abstract Slides Poster Similar
A Flatter Loss for Bias Mitigation in Cross-Dataset Facial Age Estimation
Ali Akbari, Muhammad Awais, Zhenhua Feng, Ammarah Farooq, Josef Kittler

Auto-TLDR; Cross-dataset Age Estimation for Neural Network Training
Abstract Slides Poster Similar
InsideBias: Measuring Bias in Deep Networks and Application to Face Gender Biometrics
Ignacio Serna, Alejandro Peña Almansa, Aythami Morales, Julian Fierrez
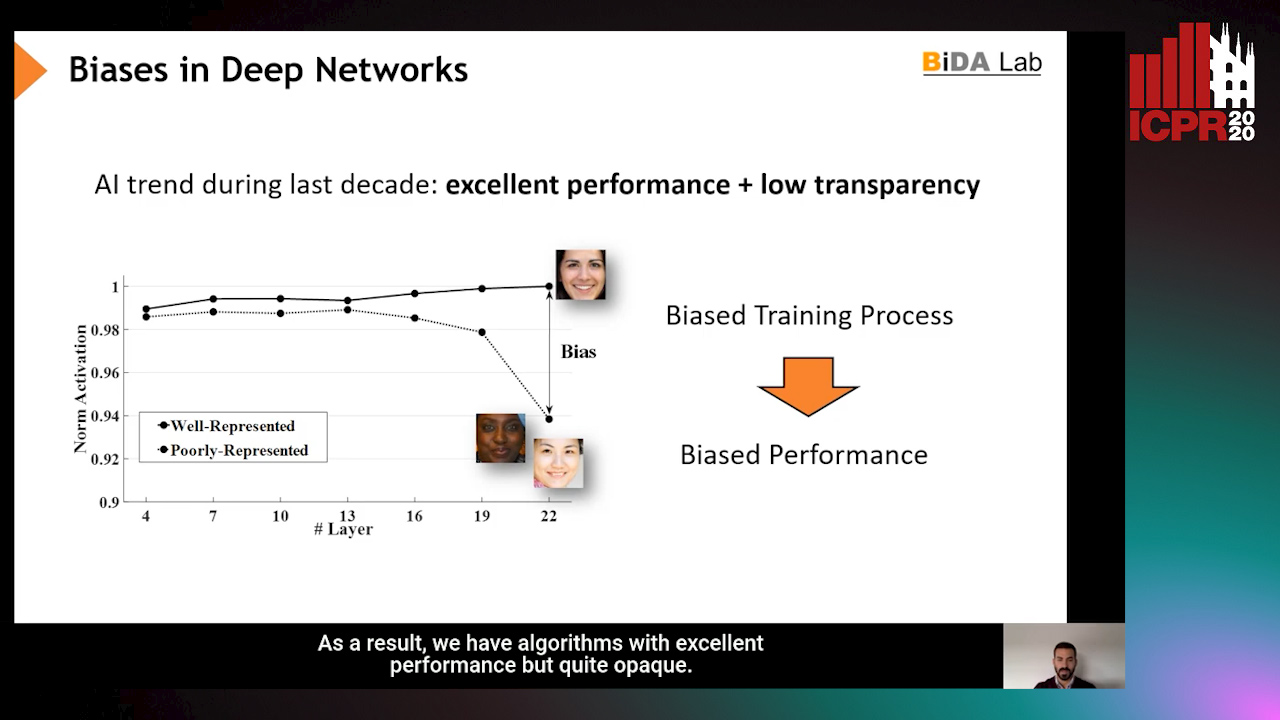
Auto-TLDR; InsideBias: Detecting Bias in Deep Neural Networks from Face Images
Abstract Slides Poster Similar
Attack-Agnostic Adversarial Detection on Medical Data Using Explainable Machine Learning
Matthew Watson, Noura Al Moubayed

Auto-TLDR; Explainability-based Detection of Adversarial Samples on EHR and Chest X-Ray Data
Abstract Slides Poster Similar
Feature-Aware Unsupervised Learning with Joint Variational Attention and Automatic Clustering
Wang Ru, Lin Li, Peipei Wang, Liu Peiyu

Auto-TLDR; Deep Variational Attention Encoder-Decoder for Clustering
Abstract Slides Poster Similar
Semi-Supervised Generative Adversarial Networks with a Pair of Complementary Generators for Retinopathy Screening
Yingpeng Xie, Qiwei Wan, Hai Xie, En-Leng Tan, Yanwu Xu, Baiying Lei

Auto-TLDR; Generative Adversarial Networks for Retinopathy Diagnosis via Fundus Images
Abstract Slides Poster Similar
Person Recognition with HGR Maximal Correlation on Multimodal Data
Yihua Liang, Fei Ma, Yang Li, Shao-Lun Huang
Auto-TLDR; A correlation-based multimodal person recognition framework that learns discriminative embeddings of persons by joint learning visual features and audio features
Abstract Slides Poster Similar
DAIL: Dataset-Aware and Invariant Learning for Face Recognition
Gaoang Wang, Chen Lin, Tianqiang Liu, Mingwei He, Jiebo Luo

Auto-TLDR; DAIL: Dataset-Aware and Invariant Learning for Face Recognition
Abstract Slides Poster Similar
Building Computationally Efficient and Well-Generalizing Person Re-Identification Models with Metric Learning
Vladislav Sovrasov, Dmitry Sidnev

Auto-TLDR; Cross-Domain Generalization in Person Re-identification using Omni-Scale Network
Learning Sparse Deep Neural Networks Using Efficient Structured Projections on Convex Constraints for Green AI
Michel Barlaud, Frederic Guyard
Auto-TLDR; Constrained Deep Neural Network with Constrained Splitting Projection
Abstract Slides Poster Similar
Improving Model Accuracy for Imbalanced Image Classification Tasks by Adding a Final Batch Normalization Layer: An Empirical Study
Veysel Kocaman, Ofer M. Shir, Thomas Baeck
Auto-TLDR; Exploiting Batch Normalization before the Output Layer in Deep Learning for Minority Class Detection in Imbalanced Data Sets
Abstract Slides Poster Similar
Is the Meta-Learning Idea Able to Improve the Generalization of Deep Neural Networks on the Standard Supervised Learning?
Auto-TLDR; Meta-learning Based Training of Deep Neural Networks for Few-Shot Learning
Abstract Slides Poster Similar