Understanding Integrated Gradients with SmoothTaylor for Deep Neural Network Attribution
Gary Shing Wee Goh,
Sebastian Lapuschkin,
Leander Weber,
Wojciech Samek,
Alexander Binder
Auto-TLDR; SmoothGrad: bridging Integrated Gradients and SmoothGrad from the Taylor's theorem perspective
Similar papers
Improving Explainability of Integrated Gradients with Guided Non-Linearity
Hyuk Jin Kwon, Hyung Il Koo, Nam Ik Cho
Auto-TLDR; Guided Non-linearity for Attribution in Convolutional Neural Networks
Abstract Slides Poster Similar
MFPP: Morphological Fragmental Perturbation Pyramid for Black-Box Model Explanations
Qing Yang, Xia Zhu, Jong-Kae Fwu, Yun Ye, Ganmei You, Yuan Zhu
Auto-TLDR; Morphological Fragmental Perturbation Pyramid for Explainable Deep Neural Network
Abstract Slides Poster Similar
A Generalizable Saliency Map-Based Interpretation of Model Outcome
Shailja Thakur, Sebastian Fischmeister
Auto-TLDR; Interpretability of Deep Neural Networks Using Salient Input and Output
Combining Similarity and Adversarial Learning to Generate Visual Explanation: Application to Medical Image Classification
Martin Charachon, Roberto Roberto Ardon, Celine Hudelot, Paul-Henry Cournède, Camille Ruppli
Auto-TLDR; Explaining Black-Box Machine Learning Models with Visual Explanation
Abstract Slides Poster Similar
How Does DCNN Make Decisions?
Yi Lin, Namin Wang, Xiaoqing Ma, Ziwei Li, Gang Bai

Auto-TLDR; Exploring Deep Convolutional Neural Network's Decision-Making Interpretability
Abstract Slides Poster Similar
Color, Edge, and Pixel-Wise Explanation of Predictions Based onInterpretable Neural Network Model

Auto-TLDR; Explainable Deep Neural Network with Edge Detecting Filters
Auto Encoding Explanatory Examples with Stochastic Paths
Cesar Ali Ojeda Marin, Ramses J. Sanchez, Kostadin Cvejoski, Bogdan Georgiev

Auto-TLDR; Semantic Stochastic Path: Explaining a Classifier's Decision Making Process using latent codes
Abstract Slides Poster Similar
Adaptive Noise Injection for Training Stochastic Student Networks from Deterministic Teachers
Yi Xiang Marcus Tan, Yuval Elovici, Alexander Binder

Auto-TLDR; Adaptive Stochastic Networks for Adversarial Attacks
From Early Biological Models to CNNs: Do They Look Where Humans Look?
Marinella Iole Cadoni, Andrea Lagorio, Enrico Grosso, Jia Huei Tan, Chee Seng Chan

Auto-TLDR; Comparing Neural Networks to Human Fixations for Semantic Learning
Abstract Slides Poster Similar
Zoom-CAM: Generating Fine-Grained Pixel Annotations from Image Labels
Xiangwei Shi, Seyran Khademi, Yunqiang Li, Jan Van Gemert
Auto-TLDR; Zoom-CAM for Weakly Supervised Object Localization and Segmentation
Abstract Slides Poster Similar
A Multilinear Sampling Algorithm to Estimate Shapley Values
Auto-TLDR; A sampling method for Shapley values for multilayer Perceptrons
Abstract Slides Poster Similar
Generalization Comparison of Deep Neural Networks Via Output Sensitivity
Mahsa Forouzesh, Farnood Salehi, Patrick Thiran
Auto-TLDR; Generalization of Deep Neural Networks using Sensitivity
Explainable Feature Embedding Using Convolutional Neural Networks for Pathological Image Analysis
Kazuki Uehara, Masahiro Murakawa, Hirokazu Nosato, Hidenori Sakanashi
Auto-TLDR; Explainable Diagnosis Using Convolutional Neural Networks for Pathological Image Analysis
Abstract Slides Poster Similar
Improving Batch Normalization with Skewness Reduction for Deep Neural Networks
Pak Lun Kevin Ding, Martin Sarah, Baoxin Li
Auto-TLDR; Batch Normalization with Skewness Reduction
Abstract Slides Poster Similar
Towards Explaining Adversarial Examples Phenomenon in Artificial Neural Networks
Ramin Barati, Reza Safabakhsh, Mohammad Rahmati
Auto-TLDR; Convolutional Neural Networks and Adversarial Training from the Perspective of convergence
Abstract Slides Poster Similar
Verifying the Causes of Adversarial Examples
Honglin Li, Yifei Fan, Frieder Ganz, Tony Yezzi, Payam Barnaghi

Auto-TLDR; Exploring the Causes of Adversarial Examples in Neural Networks
Abstract Slides Poster Similar
On-Manifold Adversarial Data Augmentation Improves Uncertainty Calibration
Kanil Patel, William Beluch, Dan Zhang, Michael Pfeiffer, Bin Yang

Auto-TLDR; On-Manifold Adversarial Data Augmentation for Uncertainty Estimation
Adversarially Training for Audio Classifiers
Raymel Alfonso Sallo, Mohammad Esmaeilpour, Patrick Cardinal
Auto-TLDR; Adversarially Training for Robust Neural Networks against Adversarial Attacks
Abstract Slides Poster Similar
Contextual Classification Using Self-Supervised Auxiliary Models for Deep Neural Networks
Sebastian Palacio, Philipp Engler, Jörn Hees, Andreas Dengel

Auto-TLDR; Self-Supervised Autogenous Learning for Deep Neural Networks
Abstract Slides Poster Similar
Accuracy-Perturbation Curves for Evaluation of Adversarial Attack and Defence Methods
Auto-TLDR; Accuracy-perturbation Curve for Robustness Evaluation of Adversarial Examples
Abstract Slides Poster Similar
InsideBias: Measuring Bias in Deep Networks and Application to Face Gender Biometrics
Ignacio Serna, Alejandro Peña Almansa, Aythami Morales, Julian Fierrez
Auto-TLDR; InsideBias: Detecting Bias in Deep Neural Networks from Face Images
Abstract Slides Poster Similar
Classifying Eye-Tracking Data Using Saliency Maps
Shafin Rahman, Sejuti Rahman, Omar Shahid, Md. Tahmeed Abdullah, Jubair Ahmed Sourov
Auto-TLDR; Saliency-based Feature Extraction for Automatic Classification of Eye-tracking Data
Abstract Slides Poster Similar
Deep Learning on Active Sonar Data Using Bayesian Optimization for Hyperparameter Tuning
Henrik Berg, Karl Thomas Hjelmervik

Auto-TLDR; Bayesian Optimization for Sonar Operations in Littoral Environments
Abstract Slides Poster Similar
FastSal: A Computationally Efficient Network for Visual Saliency Prediction
Auto-TLDR; MobileNetV2: A Convolutional Neural Network for Saliency Prediction
Abstract Slides Poster Similar
Optimal Transport As a Defense against Adversarial Attacks
Quentin Bouniot, Romaric Audigier, Angélique Loesch

Auto-TLDR; Sinkhorn Adversarial Training with Optimal Transport Theory
Abstract Slides Poster Similar
Confidence Calibration for Deep Renal Biopsy Immunofluorescence Image Classification
Federico Pollastri, Juan Maroñas, Federico Bolelli, Giulia Ligabue, Roberto Paredes, Riccardo Magistroni, Costantino Grana
Auto-TLDR; A Probabilistic Convolutional Neural Network for Immunofluorescence Classification in Renal Biopsy
Abstract Slides Poster Similar
Explanation-Guided Training for Cross-Domain Few-Shot Classification
Jiamei Sun, Sebastian Lapuschkin, Wojciech Samek, Yunqing Zhao, Ngai-Man Cheung, Alexander Binder

Auto-TLDR; Explaination-Guided Training for Cross-Domain Few-Shot Classification
Abstract Slides Poster Similar
Boundary Optimised Samples Training for Detecting Out-Of-Distribution Images
Luca Marson, Vladimir Li, Atsuto Maki
Auto-TLDR; Boundary Optimised Samples for Out-of-Distribution Input Detection in Deep Convolutional Networks
Abstract Slides Poster Similar
HFP: Hardware-Aware Filter Pruning for Deep Convolutional Neural Networks Acceleration
Fang Yu, Chuanqi Han, Pengcheng Wang, Ruoran Huang, Xi Huang, Li Cui

Auto-TLDR; Hardware-Aware Filter Pruning for Convolutional Neural Networks
Abstract Slides Poster Similar
Norm Loss: An Efficient yet Effective Regularization Method for Deep Neural Networks
Theodoros Georgiou, Sebastian Schmitt, Thomas Baeck, Wei Chen, Michael Lew
Auto-TLDR; Weight Soft-Regularization with Oblique Manifold for Convolutional Neural Network Training
Abstract Slides Poster Similar
CCA: Exploring the Possibility of Contextual Camouflage Attack on Object Detection
Shengnan Hu, Yang Zhang, Sumit Laha, Ankit Sharma, Hassan Foroosh

Auto-TLDR; Contextual camouflage attack for object detection
Abstract Slides Poster Similar
Attack-Agnostic Adversarial Detection on Medical Data Using Explainable Machine Learning
Matthew Watson, Noura Al Moubayed

Auto-TLDR; Explainability-based Detection of Adversarial Samples on EHR and Chest X-Ray Data
Abstract Slides Poster Similar
Kernel-Based LIME with Feature Dependency Sampling
Sheng Shi, Yangzhou Du, Fan Wei
Auto-TLDR; Local Interpretable Model-agnostic Explanation with Feature Dependency Sampling
Abstract Slides Poster Similar
Beyond Cross-Entropy: Learning Highly Separable Feature Distributions for Robust and Accurate Classification
Arslan Ali, Andrea Migliorati, Tiziano Bianchi, Enrico Magli

Auto-TLDR; Gaussian class-conditional simplex loss for adversarial robust multiclass classifiers
Abstract Slides Poster Similar
RNN Training along Locally Optimal Trajectories via Frank-Wolfe Algorithm
Yun Yue, Ming Li, Venkatesh Saligrama, Ziming Zhang

Auto-TLDR; Frank-Wolfe Algorithm for Efficient Training of RNNs
Abstract Slides Poster Similar
Neuron-Based Network Pruning Based on Majority Voting
Ali Alqahtani, Xianghua Xie, Ehab Essa, Mark W. Jones
Auto-TLDR; Large-Scale Neural Network Pruning using Majority Voting
Abstract Slides Poster Similar
Probability Guided Maxout
Claudio Ferrari, Stefano Berretti, Alberto Del Bimbo

Auto-TLDR; Probability Guided Maxout for CNN Training
Abstract Slides Poster Similar
The Color Out of Space: Learning Self-Supervised Representations for Earth Observation Imagery
Stefano Vincenzi, Angelo Porrello, Pietro Buzzega, Marco Cipriano, Pietro Fronte, Roberto Cuccu, Carla Ippoliti, Annamaria Conte, Simone Calderara

Auto-TLDR; Satellite Image Representation Learning for Remote Sensing
Abstract Slides Poster Similar
Towards Tackling Multi-Label Imbalances in Remote Sensing Imagery
Dominik Koßmann, Thorsten Wilhelm, Gernot Fink
Auto-TLDR; Class imbalance in land cover datasets using attribute encoding schemes
Abstract Slides Poster Similar
An Invariance-Guided Stability Criterion for Time Series Clustering Validation
Florent Forest, Alex Mourer, Mustapha Lebbah, Hanane Azzag, Jérôme Lacaille

Auto-TLDR; An invariance-guided method for clustering model selection in time series data
Abstract Slides Poster Similar
Trainable Spectrally Initializable Matrix Transformations in Convolutional Neural Networks
Michele Alberti, Angela Botros, Schuetz Narayan, Rolf Ingold, Marcus Liwicki, Mathias Seuret
Auto-TLDR; Trainable and Spectrally Initializable Matrix Transformations for Neural Networks
Abstract Slides Poster Similar
F-Mixup: Attack CNNs from Fourier Perspective
Xiu-Chuan Li, Xu-Yao Zhang, Fei Yin, Cheng-Lin Liu

Auto-TLDR; F-Mixup: A novel black-box attack in frequency domain for deep neural networks
Abstract Slides Poster Similar
A Delayed Elastic-Net Approach for Performing Adversarial Attacks
Brais Cancela, Veronica Bolon-Canedo, Amparo Alonso-Betanzos

Auto-TLDR; Robustness of ImageNet Pretrained Models against Adversarial Attacks
Abstract Slides Poster Similar
Defense Mechanism against Adversarial Attacks Using Density-Based Representation of Images
Yen-Ting Huang, Wen-Hung Liao, Chen-Wei Huang
Auto-TLDR; Adversarial Attacks Reduction Using Input Recharacterization
Abstract Slides Poster Similar
Variational Inference with Latent Space Quantization for Adversarial Resilience
Vinay Kyatham, Deepak Mishra, Prathosh A.P.

Auto-TLDR; A Generalized Defense Mechanism for Adversarial Attacks on Data Manifolds
Abstract Slides Poster Similar
Revisiting Graph Neural Networks: Graph Filtering Perspective
Hoang Nguyen-Thai, Takanori Maehara, Tsuyoshi Murata
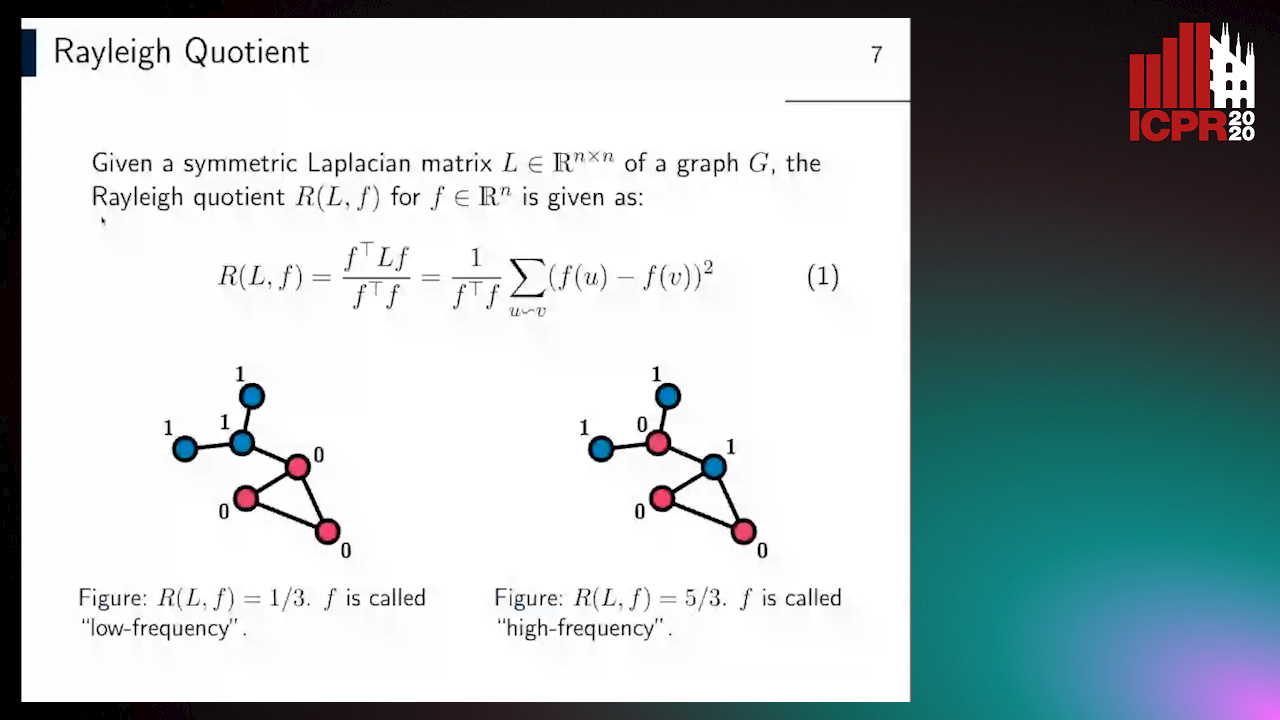
Auto-TLDR; Two-Layers Graph Convolutional Network with Graph Filters Neural Network
Abstract Slides Poster Similar
Bayesian Active Learning for Maximal Information Gain on Model Parameters
Kasra Arnavaz, Aasa Feragen, Oswin Krause, Marco Loog
Auto-TLDR; Bayesian assumptions for Bayesian classification
Abstract Slides Poster Similar
Transformer-Encoder Detector Module: Using Context to Improve Robustness to Adversarial Attacks on Object Detection
Faisal Alamri, Sinan Kalkan, Nicolas Pugeault

Auto-TLDR; Context Module for Robust Object Detection with Transformer-Encoder Detector Module
Abstract Slides Poster Similar